Apple’s iOS has always been crowned as one of the most secure mobile operating systems out there, especially compared to Android. For this reason (amongst others), most organisations use iPhones as enterprise devices instead of Android. A report claims that iOS devices are more vulnerable to phishing and web content threats than Android. Here’s what the study reveals about the situation and other details about phishing attacks.
A report by Lookout has observed an interesting trend: iOS devices are more vulnerable to phishing and web content threats than Android devices. The report says that whether your IT and security teams have to oversee 100 mobile devices or 10,000, they want to minimize the number of variations they have to deal with, due to which iOS remains their default choice. That is also why it is more prevalent in enterprises than Android.
It notes that there are more than two times the number of iOS devices across the Lookout customer base than Android devices. The report claims that 19% of enterprise iOS devices were exposed to at least one mobile phishing attack in each of the first three quarters of 2024, compared to 10.9% of enterprise Android devices.
It is important to note that mobile phishing, smishing, and executive impersonation attacks don’t rely on certain operating systems to carry out their malicious intent like malware does. Every device is vulnerable to this threat vector – putting every employee’s identity, password, and multi-factor authentication at risk. iOS devices are more vulnerable to phishing and web content threats than Android likely because there are a hugher volume of iOS devices being used as enterprise phones.
Read More: Samsung Galaxy S24, Galaxy S24 Ultra Enterprise Edition Smartphones Launched in India: Check Details
Trends Amongst Enterprise Phishing Attacks
Enterprises are facing a surge in phishing attacks aimed at stealing sensitive credentials. Compared to the previous quarter, Lookout observed a 17% rise in these attacks. Cybercriminals are becoming more sophisticated, employing tactics like social engineering and well-disguised phishing pages to trick users.
The number of malicious apps detected has jumped by a worrying 32%. These apps often pose as legitimate tools or games, but they pack hidden malware that can steal data, spy on users, or even take control of devices. The report also sheds light on the top vulnerabilities found in mobile browsers and apps. Two stand out in particular:
- Heap-Based Buffer Overflows: These vulnerabilities can be exploited to corrupt memory and crash apps, or even allow attackers to execute malicious code.
- Type Confusion Bugs: These flaws can allow attackers to execute arbitrary code, potentially taking complete control of a device.
Every mobile device has a web browser, and the most common vulnerabilities that Lookout observes tend to be in the various engines and components of these browsers. Most commonly, a successful exploit of these vulnerabilities could grant the attacker the ability to remotely execute code on the device. They are also typically exploited via a maliciously crafted webpage, which could be delivered via one of the many Messaging apps that mobile users have installed.
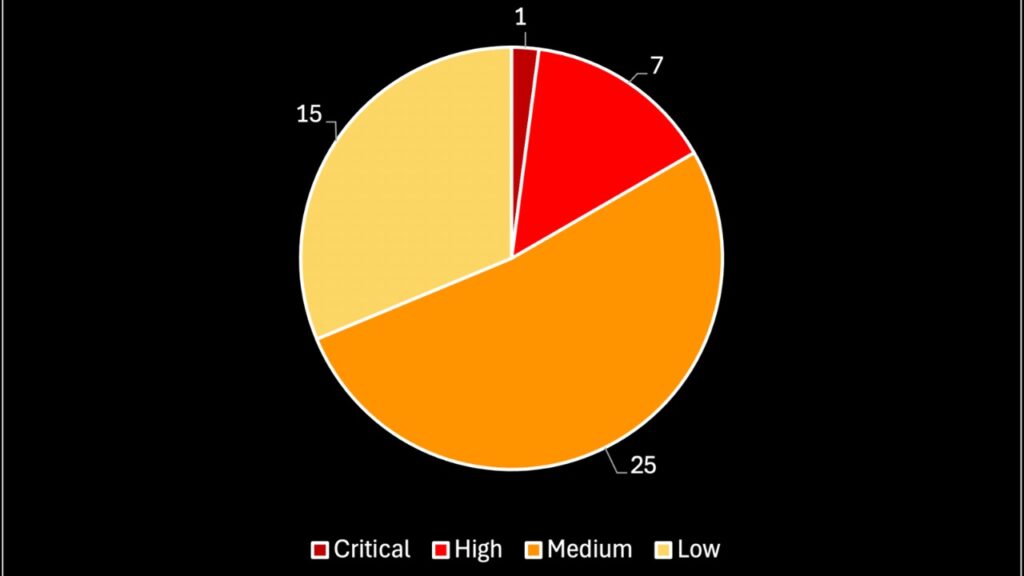
All of the vulnerabilities Lookout mentioned affect Chromium-based browsers. Chromium is an open-source project that Google maintains and develops, but is used broadly across browsers including Microsoft Edge, Opera, and more. The company also noted five most common mobile App vulnerabilities outside of Browser vulnerabilities. These included:
EvilVideo (Telegram)
EvilVideo is associated with a zero-day vulnerability in the Telegram app for Android. Attackers exploit it to deliver CypherRAT, which is built on the commodity spyware tool SpyNote.
GalaxyStore-MultiCVE-2023-21433-21434 (Samsung Galaxy Store)
These two vulnerabilities exist in the Galaxy store app and allow attackers to arbitrarily install apps from the Galaxy Store as well as execute JavaScript by launching a web page.
Samsung-CVE-2021-25337 (Samsung TTS)
A vulnerability due to improper access control in clipboard service in Samsung mobile devices allows untrusted applications to read or write certain local files.
Authy-CVE-2024-39891 (Authy)
A vulnerability in the Twilio Authy API on both iOS and Android that allowed attackers to access phone number registration information for various online services.
TikTok-CVE-2022-28799 (TikTok)
A vulnerability in TikTok on Android that allows account takeover. An attacker could achieve this by sending a crafted URL that forces TikTok to load an attacker-controlled website.
Security misconfigurations are a ticking time bomb for mobile users. These flaws leave your device and your precious data exposed to a wide range of attacks, both known and unknown. Imagine your personal information, financial details, and private conversations falling into the wrong hands – that’s the risk you face with a misconfigured device. Lookout figured out that these were the top device misconfigurations:
Out of Date OS (31.1%)
Out of date operating system (OS) versions, especially on iOS devices, can leave a device and the data on it vulnerable to known and unknown exploits.
Out of date ASPL (12.3%)
Android Security Patch Levels (ASPLs) are released by Google to patch new and known vulnerabilities in Android apps, Android OS, and even hardware components.
No device lock (18.8%)
Locking a mobile device is a basic form of securing it. Some users might disable the device lock to make it easier to open their device, which is a security risk.
Unencrypted (4.5%)
This implies that the device doesn’t have a password, pin, biometric recognition, or pattern authentication enabled.


